ETC Proof of Work Course: 10. The POW Permissionless Paradox
You can listen to or watch this video here:
In the previous class, 9, we talked about the meaning of immutability in proof of work (POW) blockchains.
We explained how a philosophy of immutability can protect users’ accounts, balances, and dapps’ past and future history.
Another strong principle in public POW blockchains is permissionlessness.
However, in this class, 10, we will explain that there is a paradox in the permissionless paradigm in POW blockchains.
Contrary to what would be expected, permissionlessness is not necessarily good in all situations!
What Is Permissionlessness?
Permissionlessness means that anyone in the world can run nodes, mine, have accounts and balances, and use proof of work blockchains such as Ethereum Classic (ETC) and Bitcoin (BTC) at will without the need for consent or approvals by any person, entity, or government.
In contrast, traditional banking systems are permissioned: Because our money is in custody of the banks, then the only way to access it is through their proprietary websites, apps, or branch offices, and we have to prove our identity so they allow us to withdraw or move our own currency.
In POW blockchains, at the raw level, just by downloading the software, anyone from anywhere can join the system and start sending and receiving money.
The Permissionless Paradox
However, POW blockchain permissionlessness has a paradox.
The permissionless paradox in POW networks is this:
To maximize permissionlessness in a POW blockchain, you must reduce permissionlessness in the community of people that most influences it.
Or, to put it more bluntly, a POW blockchain social layer should NOT be permissionless.
In a POW operating network, permissioned access is bad. In the POW blockchain community, permissioned access is good.
What Is Permissionness?
Contrary to permissionlessness, permissionness means that people must be vetted and allowed to participate in a POW blockchain community only if they share the values of the system.
If they don’t agree with the principles, or if they say they agree verbally but don’t show a consistent behavior in practice, then they should be excluded from the community.
For example, if a core principle of ETC is immutability, whoever proposes to reverse the chain or do an irregular state change for any reason, then that person should be banned from participating in any of the community assets.
By “community assets” it is meant the public forums that are used by community members to express their opinions or work for the blockchain in question.
What Is Security in a POW Blockchain?
Security in a proof of work blockchain is to depend as least as possible on trusted third parties.
Trusted third parties are security holes because they hold our wealth and they hold our information, but they can make mistakes, commit fraud, be controlled by tyrannic governments, or abuse their position of trust.
In proof of work networks, the community of people that most influences the system are a kind of trusted third party because they are the ones who maintain the protocol, propose new rules, and influence the rest of the ecosystem as to the direction of the blockchain.
This is why, special attention and care must exist when admitting members to the community.
What Is Operating Network Security?
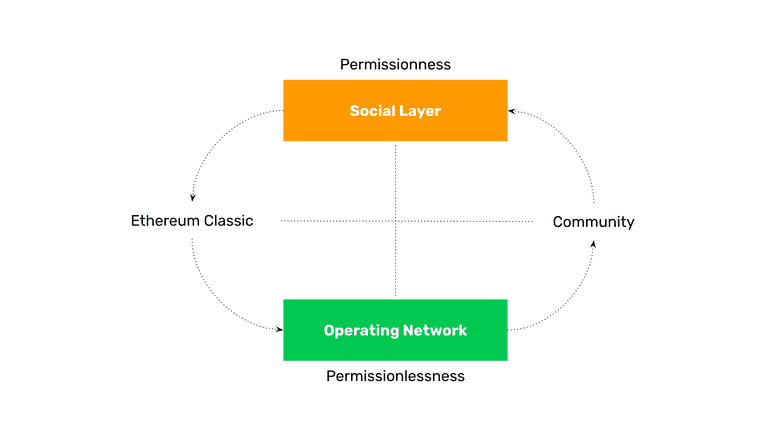
To explain the rationale for this approach it is worth explaining the security model of POW blockchains.
A blockchain is a group of nodes and miners owned and operated by people. The live network itself, with computers running the software protocol, may be called the operating network.
This is the environment that is protected by the POW consensus mechanism and holds the database with accounts, balances, and dapps which is called “the blockchain”.
This physical layer that represents the operating network is what provides the services of the blockchain to everyone on a global scale, and THIS is what should be permissionless and free to use by the whole world.
What Is Social Layer Security?
The social layer of a blockchain is all the people who own the nodes and miners, the developers who manage the base protocol, entrepreneurs who build dapps, any nonprofit organizations that support the system, and the many scientists and volunteers who participate on a daily basis supporting and maintaining the network.
Because nodes and miners are located all around the world, and they are the ones who would have to run the software with the rules of the system to implement and deploy changes, it is very difficult for them to accept on a mass scale any controversial changes that would corrupt or degrade the system. This is what is called the coordination problem.
However, the more dedicated core community is the part of the social layer that wields the most influence in the system. From this group is that bad changes could be introduced.
What Are the Threats at the Social Layer?
Think of this problem: If a core principle of ETC is permissionlessness, then why should whoever proposes new rules that would reduce or eliminate permissionlessness be banned from participating in any of the community assets?
Do you see the paradox?
However, the seemingly unsolvable problem is actually resolved when we realize that the permissioness rule only applies at the social layer, where humans tend to have disagreements and usually try to cheat each others when competing for control.
The threat is that bad changes that would make the system centralized, thus permissioned, could be and have been introduced through this layer.
How Does Permissionness Reduce Risk at the Social Layer?
Change in POW blockchains should be slow, and the decision process on new rules should be long and thoroughly debated.
Systems such as Bitcoin and ETC are not web apps or interesting tech gadgets on our phones. And, innovation is NOT the goal of highly secure public blockchains.
These platforms are systems of money, property, agreements, and basic rights on a global scale for anyone in the world regardless of their human condition.
When changes are proposed by people with no understanding or bad actors who persist in corrupting and degrading the system, then excluding these individuals from the core community reduces the frequency of these attacks, thus reducing the risk of bad changes flowing through to the operating network.
Thank you for reading this article!
To learn more about ETC please go to: https://ethereumclassic.org
